Let’s look at each of these pillars in more detail:
Capabilities for transparency and sovereigntyCustomers want to gain the benefits of the cloud without losing the control and agency over operations they have in their own data center. As described in an
earlier post, Google Cloud offers extensive capabilities today to ensure sovereignty over data, software, and operations. We allow you to configure the locations where your data is stored, where your encryption keys are stored, and where your data can be accessed from. We give you the ability to manage your own encryption keys, even storing them outside Google’s infrastructure. Using our External Key Management service, you have the ability
to deny any request by Google to access encryption keys necessary to decrypt customer data at rest for any reason. We offer the
ability to monitor and approve access to your data or configurations by Google Cloud support and engineering based on specific justifications and context, so you have visibility and control over insider access. Our
Confidential Computing services offer the ability to keep your data encrypted (and therefore isolated from cloud insiders or members of your own operations team) while it’s being processed.
Pioneering a trusted and scalable zero trust architecture As the pioneer in zero trust computing, we’ve learned a great deal about the transformative benefits but also the challenges of operating in this model. For Google, zero trust is not the latest marketing buzzword or trend to attach to—it’s how we have operated and helped to protect our internal operations over the last decade.
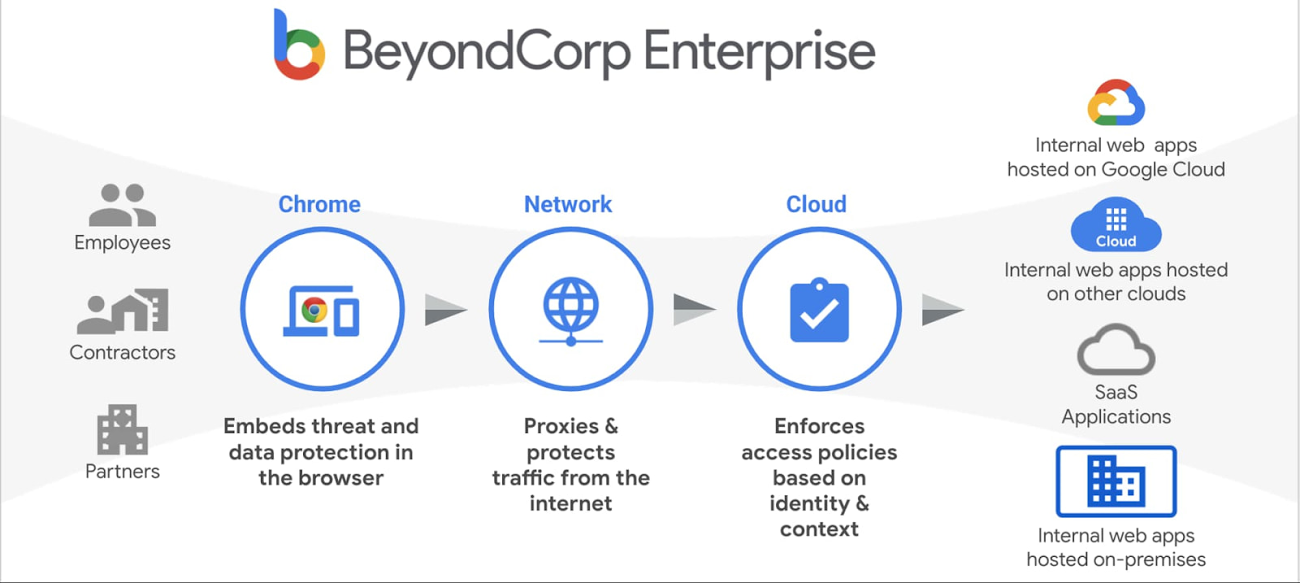
BeyondCorp is our model for zero trust access that protects Google’s own applications. It establishes trust in users based on identity, context, and the state of their device, not just the ability to connect to the corporate network.
BeyondProd is our model for operating production services securely at scale. It implements safeguards such as mutually authenticated service endpoints, transport security, edge termination with global load balancing and denial of service protection, end-to-end code provenance, and runtime sandboxing to ensure that only known, trusted, and specifically-authorized callers can utilize a service. Services are constrained to use only authorized code and configurations, and run only in authorized, verified environments, preventing attackers from performing actions that allow them to expand their reach.
We in turn productize and make these zero trust capabilities available to our customers. Earlier this year,
we announced the availability of BeyondCorp Enterprise, a commercial version of our zero trust access platform, and many of the capabilities of BeyondProd are embedded in
Anthos, our managed application platform, in features like
Binary Authorization and
Anthos Service Mesh. Combined with
Chronicle, our security analytics platform, we can deliver secure computing from user to network to app to data plus threat detection and investigation across these surfaces, even for organizations that do not run their systems in our cloud.